1. BGP Hijacking and Route Leaks – Ongoing Internet Threats
Although Border Gateway Protocol (BGP) is the backbone of the internet, it was not originally designed with security as a priority. As a result, incidents such as BGP hijacking and route leaks continue to impact global connectivity.
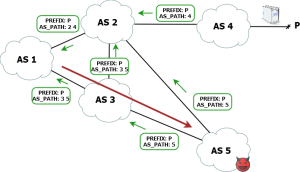
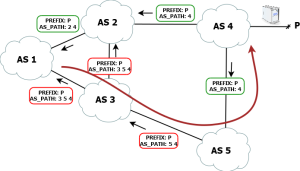
A BGP hijack occurs when an autonomous system (AS) advertises IP prefixes it does not legitimately own. This can cause:
-
Traffic interception (man-in-the-middle attacks)
-
Service outages
-
Traffic misrouting and increased latency
Route leaks, often caused by misconfiguration, can unintentionally propagate incorrect routes across multiple networks, disrupting internet stability.
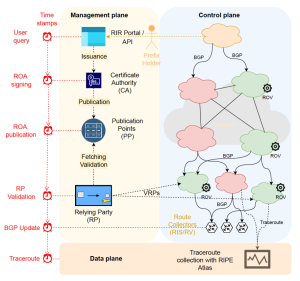
2. RPKI – A Necessary but Slowly Adopted Solution
RPKI (Resource Public Key Infrastructure) provides cryptographic validation for BGP route announcements, ensuring that only authorized ASes can advertise specific IP prefixes.
Major providers such as Google and Cloudflare have implemented RPKI validation, significantly reducing their exposure to routing attacks. However, global adoption remains uneven, leaving parts of the internet vulnerable.
3. Best Practices for Securing BGP Today
To improve BGP security, network operators are encouraged to:
-
Enable RPKI route origin validation
-
Implement strict prefix filtering
-
Use BGP monitoring and alerting tools
-
Apply max-prefix limits and route dampening